Manipulations on databases
By Amitay Dan
Disclaim:This article is only for study and public knowledge,
many people don't see email and ID reset as something to secure.
My motivation is to change this.
Lead
While
looking at databases as a target, my main idea is to find irregular
weaknesses which can give me abilities to attack the database.
In my study I was looking at the database as a fortress, and my main vision was to use manipulation as a tool to conquer it.
In my opinion using the rubbish tunnel as a way to attack the city, will be much more fun than attacking it with normal force.
Every
citadel needs water supply or someone in the gates to check the people,
but in the virtual world you can mix technique and be very creative
while having attack.
Introduction
In
my article I will share my research of how can we gain information
without using force, how can we gets databases by just asking it small
questions, knowing that every machine needs to react after it getting
orders or questions.
Sometimes
you just need to ask the website to give you new passwords after typing
email, while other times it’s about you calling the credit card issuer
by the phone, inserting random ID’s and by the answer you can gain the
users databases.
In
my article I will share how this kind of technique can be a tool for
new kind of blackmailing, political and inelegance data mining, as well
as privacy concern.
As I can see it the main target in the closes future will be to create augmented reality with people databases.
As
you know Google has a plane to sell glasses with augmented reality
abilities, in my opinion the day when we look at person faces knowing
his political opinion, email, sexual status and many more small data is
not so far from now.
Body
Let's start with giving faces to email lists
What can be done with spam list? There are many websites which are selling email list1
for later uses. Basically the idea is to sell something or to send
something to this emails, sometimes you can buy two million emails for
very cheap price.
Figure 1
As
for me I was thinking more and more about the hidden benefits behind
this kind of email list, what can be done with the most common ID in the
virtual life, the one that you carry everywhere, in every website that
asking you to register?
The
answer was to find this people in the reality, but first to gain
information on them using very common weaknesses in databases, the
reset.
Before
going there we need to go back to the beginning, how can we gets people
faces by having their emails, and how that can be the basic for our
attack?
The
social network is the most known place to gain information about
people, actually as part of Facebook system you would be able upload 2
a
file contain a huge amount of emails, and since this is the way they
work, you can use Facebook to attach to people their faces and then you
have email plus faces plus Facebook account, and that’s just the first
step in the association process.
Figure 2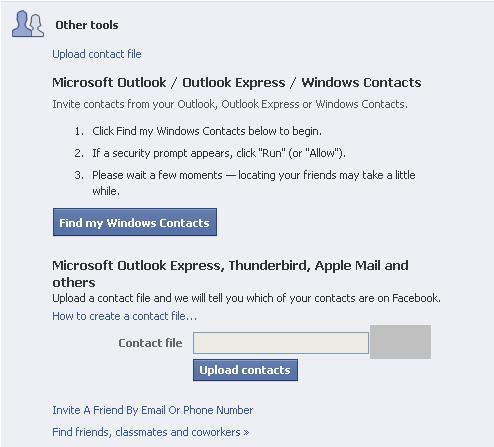
So what do we have? We do know that email lists are very common product
to buy, and they can be a way to find people faces and that lead us to
realize that this is the first step of recognizing people in the
reality, in the street at the bar or even form the video camera from our
home.
A company called Face.com #
which sold to Facebook had an apps who called “klik” this apps gave to
social network users like Facebook abilities to recognized and tag their
friend in the reality, so the technology is here and since that facial
recognition it’s not only in Facebook and social website and if you want you can play with open source as well.
Now
we should think forward and see that emails are actually the basic link
between the reality and the cyber life, so why don’t we mix all the
data about the people and make their virtual life to be known in the
street, why don’t we push their virtual identity into the physical one?
This is not philosophical question but actually a the basic behind my study.
Many
questions are being asked here, so let’s start to figure out the
solution, but first let’s see what Facebook has to say about the issue.
Facebook and me
Since
I understood that Facebook can be the best way to link between faces of
people and their email which are taken from email lists, I was trying
to ask the Facebook what they have to say about it, and here is the
story:
-----Original Message to Facebook-----
From: ***********
To:
Subject: Report a Possible Security Vulnerability
Name: Amitay Dan
E-Mail: **********
Type: db_injection
Scope: www
Description: Hi,
This week I have found a huge problem in Facebook database.
As you know Facebook gives the users the ability to find their own friend.
By
opening new email and insert in a list of mails (which can get from
spam list) I can sneak out from Facebook the whole public data of the
users.
If you do so by searching for new users by email in the search box you get get it as well.
By that every spam list, or database with email can have very easy (by script) a face, pictures of the email owner.
Please contact me as soon as possible.
Best regards,
Amitay Dan
Ethical Hacker
Hi Amitay,
This
is not a security vuln, anyone you can find via the find a friend email
looking feature has the privacy setting "allow people to find me via"
set for email.
Thanks for contacting Facebook,
Emrakul
Security
Facebook
My answer for that was:
Hello Emrakul,
Thank you for answering me.
I do know and aware to the fact you mention.
If that not a problem I do want to ask for your agreement to use my point as part of my study.
The regulators in many countries won’t accept so many people to be heart.
I would like to speak as well with someone from Facebook Israel or the relevant office.
I
do agree that people knows that email are a legitimate tools to find
them, but there are many ways to use it for bad and that should be
avoid.
As
I have found in my study while someone email account (Gmail) account is
being hacked, the hacker can sneak out the whole data of his contact
persons in the email.
Next step would be adding into the database the faces and the names which can be found by Facebook.
For
this I had no answer back until today, so maybe now people should ask
them self if they really want that every spammer or someone who have or
bought database with their emails would be able to link between their
email and the faces thanks to Facebook.
I
got not answer about the abilities to use Facebook service with bulk
amount of emails, so it seems that no one’s care over there.
Now let’s back to the bad side.
Definition of ID
In
the past ID social security number (SSN) and fingerprints where the
most common identity stamp of people, now days, the email the phone
number and nicknames are being very common ways to recognized people in
the cyber world, and that’s why there are the main target to gain
information from databases in my study.
How to cheat computer
Normally
when you see a weapon pointing at you should know that you need to
protect yourself, yet, sometime the uses of uncommon vector to gain
access into places can be smarter.
As
you might know there are a lot of uses in women as a way to get into
data places and secure area, males are thinking different when they see a
pretty woman and most of people won’t suspect you while you carry a
baby or a child with you, it’s a good cover.
Looking at computer as the target can give us an headache, they have no emotion (yet) and they don’t care.
The
best way to make computer to be confuse is to understand that a human
made them, and then to realized step by step how to steal from them the
database with no single shot.
Starting from Linguistic Journey
Before
the battle began, we needs to gain inelegance ,and words will be our
best tools for that, after we fulfill the emails from the email list we
got with pictures names and nick names of the people we want more data
about them.
The mission will be to find places where after inserting inside emails,
we will get an answer that telling us if this email is known in the
database.
This answer is wrong website should never say what is in the database, and who the clients are.
Let’s start with searching in Google the words like:
“Reset by email” “please enter your email reset”
and see what’s happen, many website are coming with an option to send
new password to the user email, and when we got bingo we know that this
person from the email list is part of the database.
After time we can understand that looking only for the error answer like ”Email Address Not Registered”
“No account with this email address was found“ , “You have not entered an email address that we recognize. Please try again or contact the administrator”, ”E-mail address not registered or being creative” Email address already registered “ “email address is already registered” can take us very fast to websites that don’t protect their databases from attack like that.
Mostly
even if you can’t gets reaction from the website by resetting using
email , you can just try to register as a new user with a known email,
and then even the most secure system will tell you that your already
part of it (unless it’s ok to have two user in one email).
I don’t want to go deeply into the linguistic
trip but it’s very interesting to see how looking for simple words
taking you into a place where you can get many website with problems in
the databases.
It’s time to do some examples
Choosing targets
The first step is to find places where there is a benefit behind the database.
Case study #1
Sexual
preference is something that not all of the people want to share if
it’s not straight, many people are living behind the cupboard, and since
that many of them have family there are very easy target to be
blackmail.
I believe that website that giving services to this community needs to protect the privacy of the users more than others.
So
let’s began, all you need to do is to find popular website where the
user can type his email to gets new password, after it you need to see
what is the website answer.#
As mention before cases like can be a way to gain a lot of money from the victims, you actually dealing with knowledge.
People will pay you money so you don’t crash down their life.
Figure 3
Case study #2
Jihad
and freedom fighters movement are places where people like to hide,
it’s too risky for some of them to be known by the real name. In places
like that we can try as well to use the reset or registration technique# and gain inelegance about the faces behind the website.
Let other help you
Since the main idea is to know everything you can get, there are websites# that can help you to find OSINT (open source inelegance) from the internet.
Gaining data from phone systems
Many
security specialist and pen tester doing a lot of work in the internet,
but protecting phone systems from hackers and phreakers# is something more difficult.
If
you want to cancel a credit card of a person, or just know what credit
card he his holding all you need to do is to start canceling process
according to stealing.
Another option is to insert random ID into the bank or credit card issuer using wardiling attack using known bulk ID’s database.
Sometime all you need to do is to start phone recognition process and
stop it after you’re being asked to type the password, the method is
working like the internet databases.
Political agenda
Sometime
people said what is there political agenda, but if you are in the army,
in government office it’s you prefer to keep it secure.
My next step is to show out how can we get’s people political background.
Since it’s not easy to hack into the database we will do something else, we will try to signup# for email updates in the Liberation party website.
Figure 5
As
you can see the privacy of the user is not being kept, the website is
telling us that “You are already signed up” so we can connect now
between the person data and the Libertarian Party website.
Now let’s go and see what’s going on in the Democrats# website maybe they do better?
Figure 6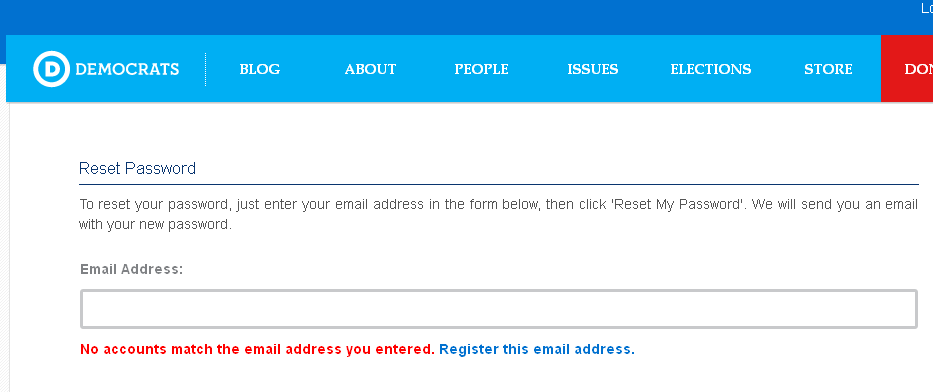
Well,
even here it’s seems that we can’t trust our privacy, the users
database is open to the public, since the system telling us that “No
accounts match the email address you entered”
Health status
Let’s
said we want to know something more useful, something that can make
people life being hell, while other can be aware of the problems around
them, why don’t we check who has AIDS or HIV.
Without going too far into the questions behind the motivation, we do need think about it a bit.
What should make people pay more money, removing fake antivirus# or blackmailing using their medical problem as a flag, pay me or I will publish that you have AIDS?
These
kinds of security problem are not normal, they are not sexy and no one
will pay money to solve them without being sew in the court. Yet, they
should concern us much more than normal ones since they can change
people life.
Thinking about the subject made me look into website who giving service to this kind of community#,and very easy I’ve the reset area where all you need to type is email#.
Figure 7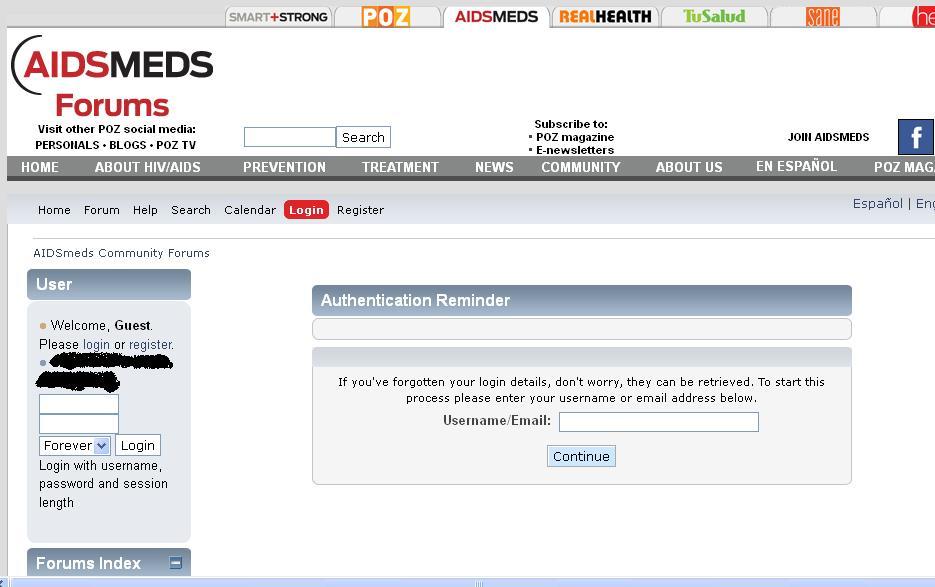
Since we needs two for tango let’s find another examples to this systematic privacy problem, even more than two#
Figure 8
Figure 9
Figure 10
Figure 11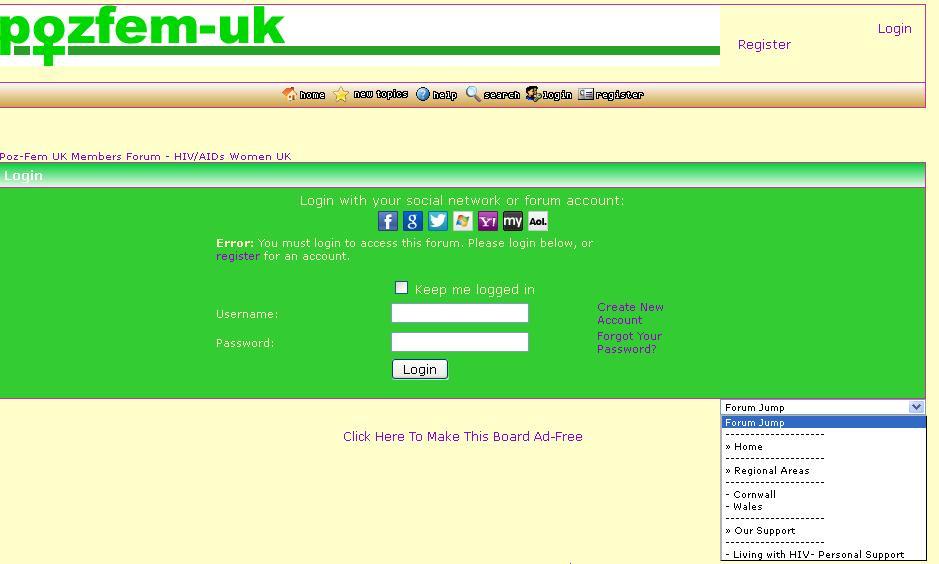
Figure 12
Now,
all you need to do is to enter the email from email list or just your
new partner’s email and see what happened, maybe the answer will be
negative - we don’t know this email, but it might be as well positive
this email known by the system and he his one of us.
Now you can take this answer and using the email you can get this face,
his full name and facebook account, and you should suspect that he or
she has HIV or Aids.
That’s not small security problem, it’s not security issue at all, it’s something else.
Forums are easy targets
Many
forums are being built based on free and popular services, so the same
problems of giving feedback while doing reset password are very common.
Time after time I have realized that forums have problems, and basically
they had much more problems than normal websites.
Manipulation and hacking
Since
I was starting this career by realizing how to break into bank account
using the phone kiosk in the front of the bank’s branch, while using the
redial bottom to get ID’s and password after decoding them# I believe that we can gets many other things we want, like information from databases by using creative ideas.
I
don’t like to use my force while it’s not needed. If you want to get
database, many times all you need to do is to think what the real user
will do if he forgets his data, and what’s the reaction of the machine
will be.
1984-2012
Well, as you can see we are going into a place that 1984#
is not a fiction, the difference is the fact that in here everybody has
the power of the government, we all can be in the closest future a
human-sniffer, who knows many things about the people around us.
In my opinion having on the way the Google glasses# which are the “Project Glass” or even starting now projects with the Recon’s android SDK# and the new camera options with augment reality, can be a fast step into the time when people will have RoboCop# abilities.
Since Apple and Google have a battle it won’t surprise me to see the answer of Apple answer for this development.
Knowing
that you can already can get a product, write some code and starts
analyzing the space around you make more sense than ever while thinking
about the uses of stolen databases.
Figure 13

Figure 14
Going wild
It’s
not any more about how to steal database by doing manipulation, or
hacking into Jihad forums, or another sensitive places like areas with
people who suffer from HIV.
With this glasses (without the ski parts) you can go into gays festivals,# record them by video tag them or crate people faces data from video in YouTube# and then create an application which showing you warning every time you see a gay, lesbian in the street.
Leaving the gay community behind, let’s think about something more creative.
Face and emails
As
you know from the beginning of my article, the uses of email list for
sell can be different in the future, no more spam but abilities to know
what is the email behinds the face, knowing that will give us abilities
to create dating application that will tell us by looking at the person
who is single and who is not. Other abilities will be to have live
sexual offender to protect your child#.
Since not everything bad, we can use the face recognition to track missing persons as well#.
Going
with this line of mind can take us into brand new places, you walk at
the street and you need something, someone else have it and he can be
recognize by the “giving application” ,so you don’t know him but he will
help you.
The future of database hacking
At
the time when we will have abilities to create databases by our digital
eyes, (and this time is almost here) hacking and stealing databases
will be much more active.
No more standing behind the computer but wearable glasses or contact lances which creating dynamic database from nothing.
Doing
counter civilian jobs as a private investigator will be different as
well, and gathering data will be in different level.
Social Engineering
Since
we will be able to start with web based databases, and then mix it with
reality based data the next level will be to use this data to hack into
the people mind, to make them believe us.
If you can know so much about a person that you never met why don’t you use it to get his Password very easy?
Automatic geo-location fishing systems
In the past advertise based on geo-location were made by SMS, thank to the tower location and the operator.
Now
days they are more and more application that send coupons since you are
close by, while thinking about it I had an idea, why don’t we use this
kind of behave to attack the surround area?
Knowing
that people want deals from the closes store around them made think
about a funny attack, an apps for the wearable glasses which are
scanning faces around you and sending them automatic phishing or Trojan
assuming to be a coupon from the closes store.
That will work for sure in countries where coupons are popular tools# , and thanks to the email list and Facebook we can do it.
Summery
This
article spoke about the idea that email lists can be a the basic tool
to hack into people life by stealing databases in creative kind of
scraping, after that this people can be found using their emails, in
website and forums, linked them to illegal activities like terror, or
just tag their political or self sexual activities, new kind of
blackmailing is just want idea.
Having
list of emails with the names and the faces can be very interesting
tools while you using them for questioning website if they knows someone
or not, or just saying, I forget my password please send me new one.
By
then the website won’t understand that while he his guarding the
database, he his actually helping the attacker to get the knowledge from
the database.
Sometimes
linking people to cyber activities can be just by trying to add theirs
emails to website newsletters system, and they are less protected than
many other system.
Facebook
and similar social services are doing a lot of thing in the world, but
the idea of using those services to linked stolen databases to people in
the street, using augmented reality is something that we will see in
the next future.
I
believe that people will pay to hacker for this augmented knowledge,
and I think that hacking database in the 21c will be much more
interesting than the past.
4
5
6
7
8
10
